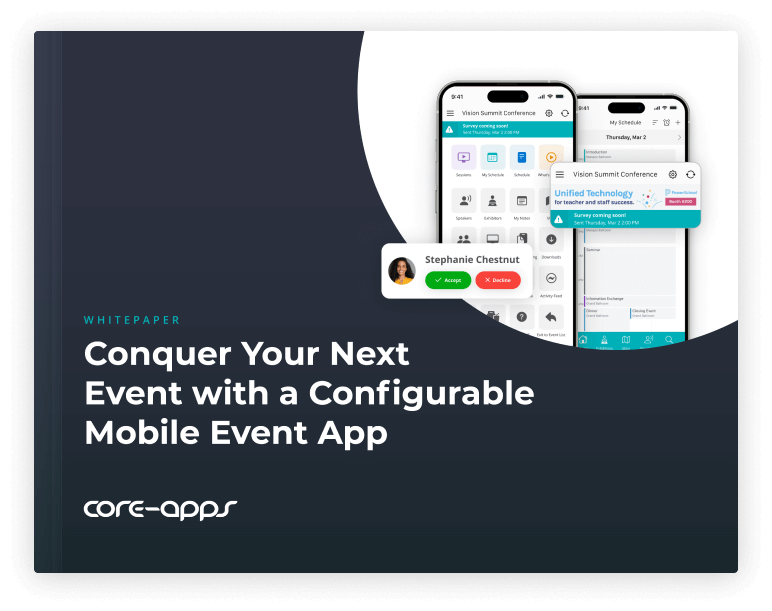
MOBILE EVENT APP
Create the event experience of your dreams.
Maximize attendee engagement with a user-friendly mobile solution from Core-Apps, the leading event app partner for conferences and trade shows. Transform session support, networking, and enhanced sponsorships from imagination to reality.
MOBILE EVENT APP
Create the event experience of your dreams.
Maximize attendee engagement with a user-friendly mobile solution from Core-Apps, the leading event app partner for conferences and trade shows. Transform session support, networking, and enhanced sponsorships from imagination to reality.

CLIENT SPOTLIGHT
Companies that trust Core-Apps, the leading event app partner for conferences and trade shows.
EVENT APPS FOR CONFERENCES AND TRADE SHOWS
Let your mobile app do the heavy lifting on your next event.
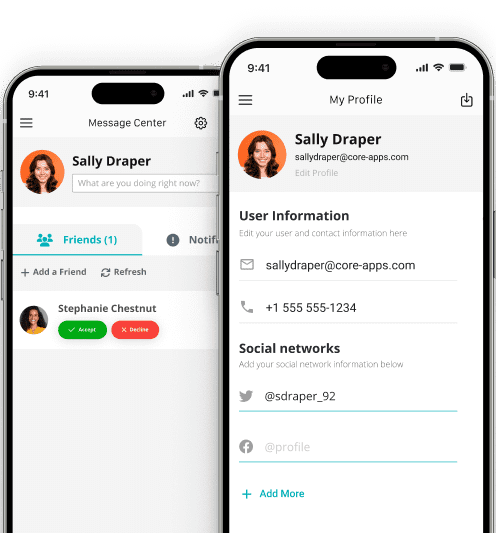
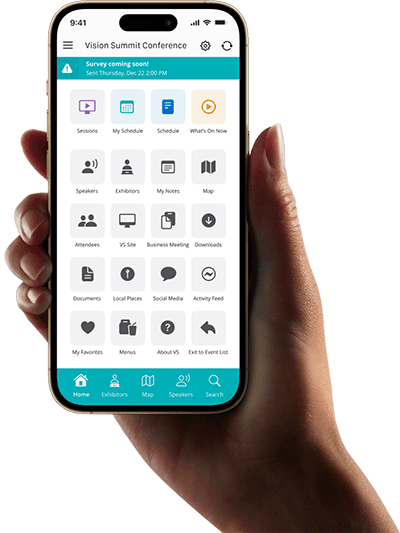
NETWORKING
Engagement opportunities attendees love.
Attendees crave connections and shared experiences. Powerful interactive features built into Core-Apps ensure your next event will keep everyone fully engaged. Create a bustling event network and strengthen connections, community, and meaningful conversations.
SPONSORSHIP
Drive better event ROI with sponsorship tools that attract and retain vendors.
Effectively manage your event sponsors and exhibitors while maximizing leads and brand awareness. Deliver more value and improve ROI through real-time data and enable your attendees to discover and engage with your sponsors, exhibitors, and stakeholders faster.

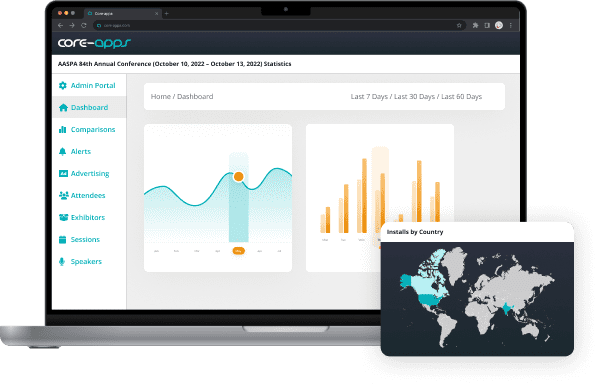
DATA
Grow your events with powerful data and analytics.
Take your event program to the next level with informed decisions. Our robust stats portal provides all the app analytics – from attendee engagement to post-event survey feedback – to help you design your event’s success. Even better, reporting on ROI and brand exposure to your sponsors and exhibitors has never been easier.
WHY CORE-APPS?
Grow your events with a powerful mobile app.
Our cost-effective total solution includes award-winning event mobile apps, event management software, and many special features – all designed to work together seamlessly.
Feature-rich solution
Improve event management support at all levels.
Seamless integration
Enjoy tools that come standard with the industry’s top CRM.
User-friendly interface
View helpful analytics in a single place.
Configurable software
Utilize the flexibility of Core-Apps to create your event’s brand, look, and feel.
Our award-winning event app powers the events and trade show industry.
What’s better than extraordinary event experiences that maximize your ROI and excite sponsors? Empowered attendees. Core-Apps runs ahead of the pack, allowing attendees to focus on what is important: networking, learning, and exchanging knowledge, all from the palm of their hand.
Associations
Impress your members with a modern event experience. Attract, engage, and retain members before, during, and after your events – all within an easy-to-use mobile app.
Corporations
Supercharge your event engagement strategy. From conferences to corporate summits and training sessions, lean on Core-Apps to enhance your corporate events, generate excitement, and increase your ROI.
Trade Shows
Maximize the impact of your trade show. Deliver powerful, engaging, and connected experiences to attendees and exhibitors through in-device messaging, meeting scheduling, banner ads, and more.
Independent Events
Bring engagement to the center of attention at your events. From consumer shows to national, regional, and niche shows, Core-Apps offers the right functionality mix to power events of any size.
CUSTOMER SUCCESS
Core-Apps powers your event experience and we empower you.

EVENT PLANNER RESOURCES
What’s the buzz?
Stay on top of trending technology, innovation, and event management insights.